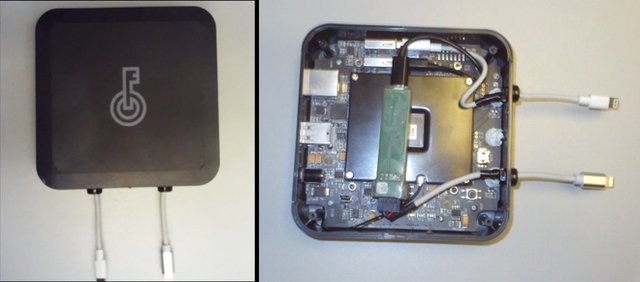
GrayShift has long been famous in the world for its GrayKey tool that can unlock iPhones, but very few people understand its operating mechanism.
Previously, many reports said that the device unlocked the iPhone or iPad by using a brute-force attack algorithm to detect the password.
The leaked user manual appears to belong to the San Diego Police Department, was written to instruct officers on how to use the device, and was found by Motherboard.
This document describes different conditions for GrayKey to connect: the device is turned off (also known as BFU – before First Unlock), the phone is turned on (After First Unlock or AFU),
To unlock the device, the document says: `GrayKey will install a piece of code (also called an agent) when the device only has 2% to 3% battery left.`

When running GrayKey, users have many choices about the type of data they want to collect on their iPhone.

A section of the documentation also describes how GrayKey is used to exhaust character passwords.
This list is provided in a file called `Crackstation-human-only.txt` containing about 1.5 billion words and passwords.
Once the `agent` code is installed, the iPhone will be placed in Airplane mode and can now disconnect from GrayKey.

Another feature of the device is called HideUI.
GrayKey and many other companies in the industry seem to be playing a cat-and-mouse game with Apple when trying to break into encrypted iPhones.
See AppleInsider